Hacker Summer Camp: BSides Las Vegas and DEF CON 2018 review

Time flies... It's already been a few months ago that BSides Las Vegas and DEF CON 2018 were held.
BSides Las Vegas was nice, although the overall quality of talks seemed to be a little higher in previous editions. This of course can be completely due to me picking exactly the wrong talks: There is simply too much to see.
DEF CON 2018 was also different than previous editions - mostly, because it was now so spread out (Caesars Palace as well as the Flamingo Las Vegas). In practice, this meant a lot of walking between the two locations. When you were attending a talk in one location, it physically wasn't possible to attend the next one unless it was located in the same or surrounding room.
Fortunately DEF CON is all about learning, doing and networking - and in that aspect it didn't disappoint.
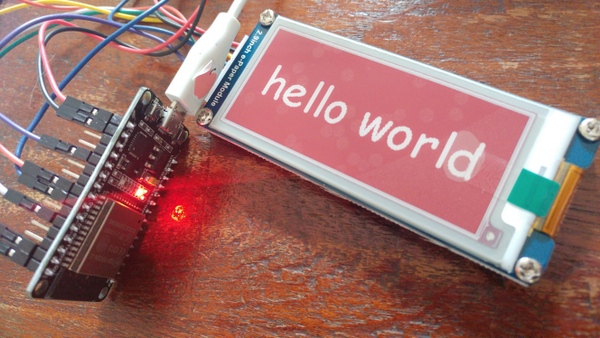
Especially for Hacker Summer Camp, I designed and built my own badge - consisting of an ESP32 [1] microprocessor running MicroPython [2], an e-Ink display, some custom Python code, and a retro cassette case. The display rotates numerous fitting images. The image was visible even when the power was disconnected, thanks to the 3-color e-Ink display.
A follow-up …
more ...


 Researching new vulnerabilities, techniques or concepts can be
time-consuming and sometimes chaotic. A streamlined workflow is
necessary to make the process as efficient as possible. This article
describes the open source tools and well-known standards that I'm
currently using for that purpose.
Researching new vulnerabilities, techniques or concepts can be
time-consuming and sometimes chaotic. A streamlined workflow is
necessary to make the process as efficient as possible. This article
describes the open source tools and well-known standards that I'm
currently using for that purpose.


